Introduction
The rapidly changing landscape of cloud security necessitates robust tools and practices. Google’s Security Command Center (SCC) offers a comprehensive suite of features to protect your data and operations. Google’s Security Command Center began responding to the increasing need for multifaceted security solutions in the cloud environment. Ongoing changes and challenges in the field of cybersecurity have guided its evolution.
Key concepts of Google Security Command Center:
|
Concept |
Description |
|
(Event/Workload) Threat detection |
Identification and analysis of potential security threats. |
|
Risk Management and Security Health Analytics (SHA) |
Near real-time identification of misconfigurations and vulnerabilities across assets and resources. |
|
Visibility |
Centralized tracking of assets and resources, facilitating the monitoring of audit logs and helping prevent the oversight of crucial logs. |
| Compliance and Reporting |
Report compliance monitoring and results by applying universally followed criteria |
For a more detailed view of the Security Command Center features, please visit: https://cloud.google.com/security/products/security-command-center?hl=en
Key Concepts
Let’s now explore each key concept and elaborate:
1 – Threat detection
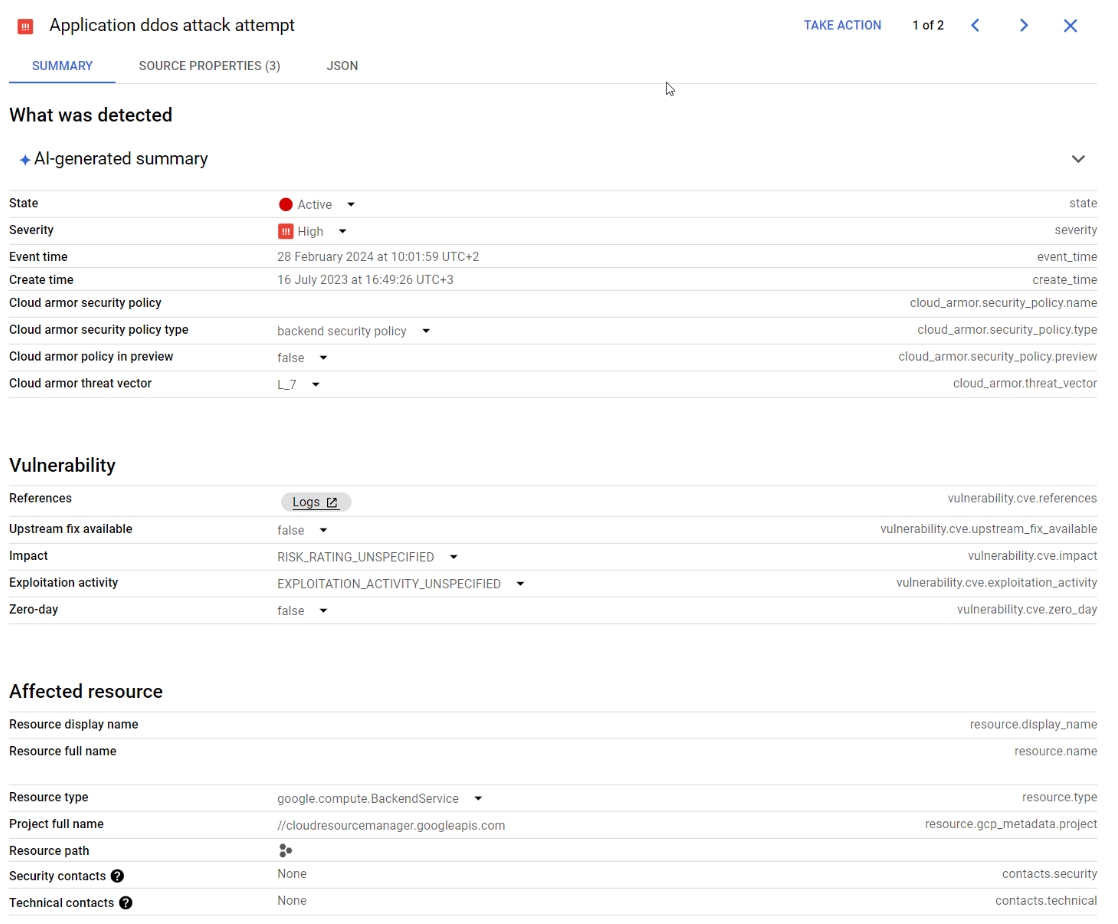
SCC can identify potential security threats, ranging from malware and brute force attacks to suspicious user activities and data exfiltration attempts, to OWASP top 10 security threats, SSH Brute Force attacks, crypto-mining, anomalies in IAM grants, and data exfiltration.
In the following screenshot, we can see an attempted DDoS attack on a real project on some of the resources in a project:
2 – Risks & Vulnerabilities
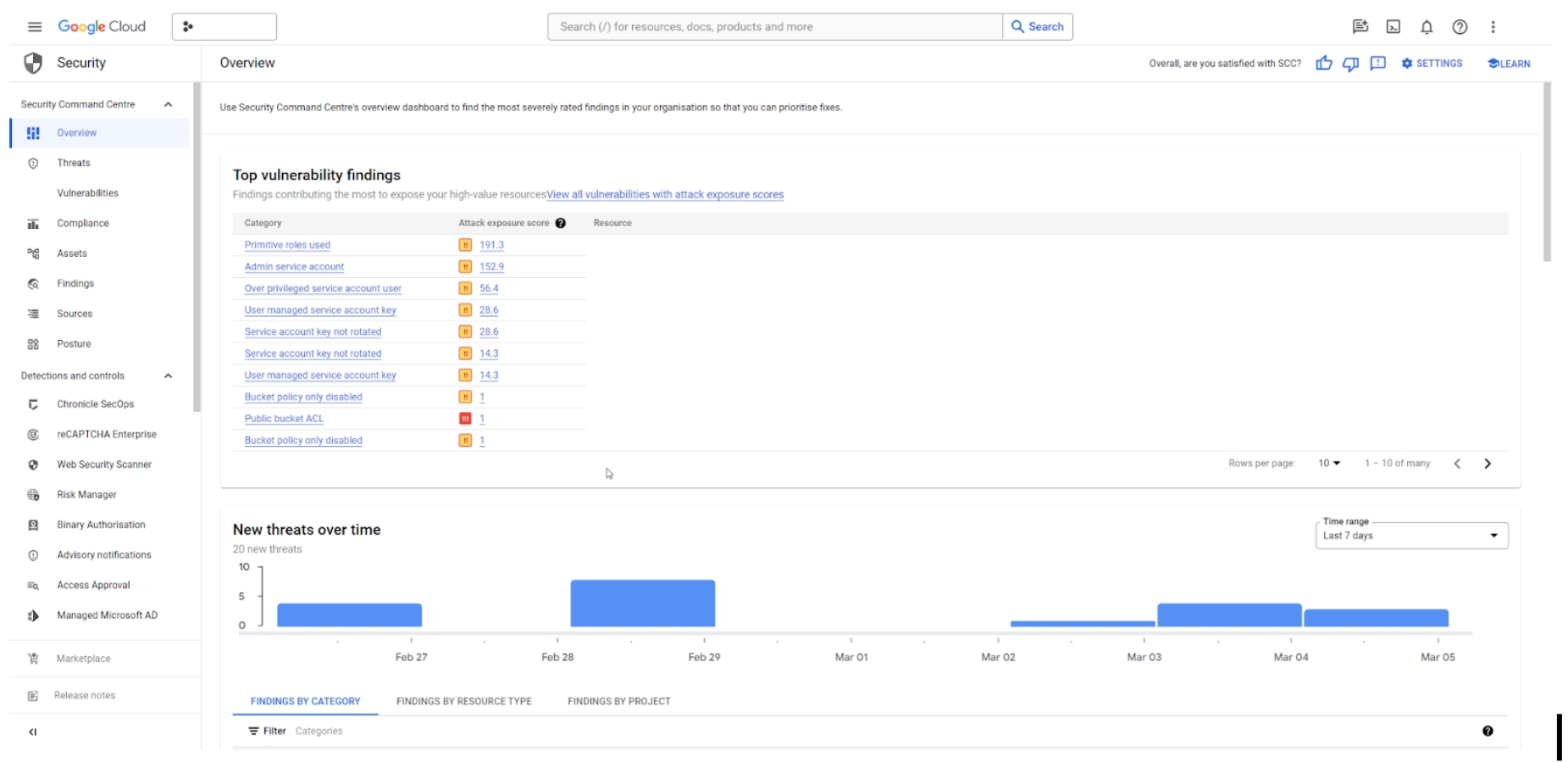
In those assets and resources, SCC can help identify misconfigurations and vulnerabilities (overarching permissions, too many permissions, public IPs still configured, open ports and so on…). This comes at near real-time updates.
3 – Visibility
Asset and resource tracking: One convenient place for collection and monitoring of the available resources in the project, specifically for the services and resources for which audit logs were turned on. Having this one central location can help prevent missing crucial logs in every service/resource. Such logs and risks are concentrated in one convenient place to look at, with all the data that’s related to the detected resource.
4 – Compliance Reporting
SCC helps security teams achieve compliance by providing reports as part of the Security Health Analytics. It continuously evaluates the Security Posture against known compliance standards, like ISO-27001, PIC DSS 3.2.1, NIST 800-53 and so on.
Conclusion
To conclude, Google Cloud’s Security Command Center is a powerful tool in a security professional’s arsenal. It centralizes, simplifies, and enhances the visibility and control over the security posture of GCP environments. Regular interaction with Cloud SCC, combined with a proactive approach to its insights, can significantly enhance the security of your Google Cloud assets.
Contact us here and let’s talk about how WideOps can advance your security goals.
About the author
My Name is Raed. I’m a Cloud Architect and part of the Security Team at WideOps LTD, a Google Cloud Premier Partner. My journey into the cloud computing world has been an eye-opener, revealing a vast landscape of technology and services that fuse, enabling us to craft stable and scalable infrastructures. This blend allows endless possibilities and rapid growth across various aspects.